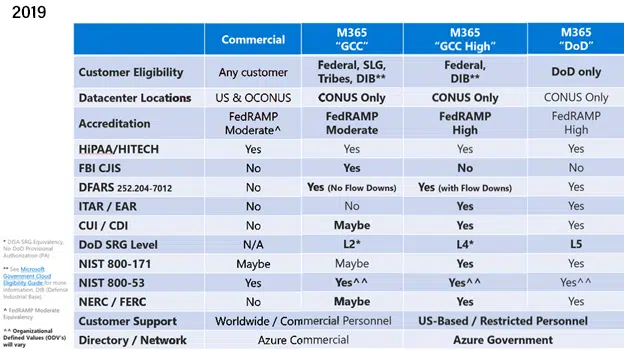
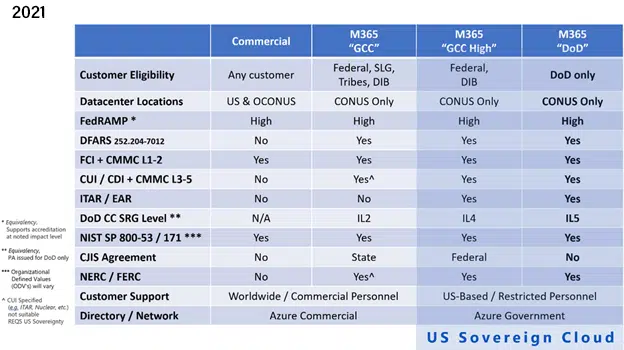
Yesterday, Richard Wakeman, Senior Director – Aerospace and Defense at Microsoft, provided a terrific update to his 2019 blog post, Understanding Compliance Between Microsoft 365 Commercial, GCC, GCC-High and DOD Offerings, providing a lot of additional detail, and answering many of the questions we at CyberSheath come across on the regular from our Defense Industrial Base (DIB) customers. Today, I’d like to cover the three most interesting and impactful assertions from the article and discuss what the changes and clarifications mean for current and future customers of Microsoft’s cloud services who have defense regulatory requirements. But let’s start with the compliance matrices:
As you can see when looking between the year 2019 and 2021 of these compliance matrices, a lot of the ambiguity in the 2019 version is removed. There are no longer “Maybes” or fine print in the cells of the table, and there is an overlay highlighting the importance of data sovereignty – more on that in a minute. You can also see the introduction of CMMC Maturity Levels and the more frequently referenced term of Federal Contract Information (FCI). Let’s talk more about these three interesting bits of information.
Microsoft 365 Government Community Cloud (GCC) High
Observation 1: Still suggested (but…is it required?)
GCC High – A common buzz word in the world of DFARS 7012 and CMMC. There’s been a lot of speculation as to whether or not Microsoft 365 services on GCC High are required if you are doing defense work, and I think Microsoft’s update makes the answer much clearer. The short answer is still maybe, as it was in 2019, but the information provided is much more prescriptive in leading DIB contractors to ask the right questions about the data they are protecting.
- Do you have the DFARS 7012 Clause in any of your Defense-related contracts?
- Do you have Controlled Unclassified Information (CUI)?
- Do you have Federal Contract Information (FCI)?
- And, with added emphasis, do you have ITAR/EAR data?
This is a simplification of the thought process, and for the sake of keeping this somewhat short, I’m avoiding the thoughtfulness and consideration that should happen around where these data sets exist, how they are stored, received, shared, but depending on how these questions are answered, it becomes clear as to which Microsoft 365 services you should be using or considering. The trouble though is, are you, as a contractor, looking through the right compliance lens? There are vendors, solutions and service providers out there that attempt to solve for a control or set of controls, attempt to deliver compliance for a particular standard (NIST 800-171, CMMC), but the fact of the matter is, all the other questions must be considered to select the right product for your business.
Much of the CyberSheath team has been born and raised in the Defense Industrial Base – we understand the challenges with interpreting these requirements and the importance of all of them, which is why I was happy to see Microsoft’s emphasis on Data Sovereignty and ITAR/EAR in their update. And, like Mr. Wakeman alluded to, security and compliance practitioners are not (usually) legal counsel, but as CyberSheath’s business is focused on delivering security and compliance for the Defense Industrial Base, we have been having these discussions with our customers for years, helping them navigate the decision-making process around their data protection requirements.
If you only receive well-defined non-ITAR/EAR CUI through a secure file transfer portal, and you keep that data on on-prem file services, do you need GCC, or GCC High? Probably not. On the other hand, if you are exchanging ITAR/EAR via cloud email services, collaborating with Defense customers on Microsoft 365 – Teams, SharePoint, OneDrive – You’re going to want to strongly consider GCC High because of the US sovereignty for all the supporting Azure infrastructure and services to meet your ITAR/EAR requirements.
Microsoft 365 GCC (Not High)
Observation 2: Now with Flow Downs!
“If I can’t flow down the DFARS 7012 requirement to Microsoft, how can I ensure that I can comply with sub-paragraphs (c)-(g) on incident reporting?” This was a deal breaker for many of those considering GCC vs. GCC High for quite some time, but it appears that Microsoft is now accepting flow down of the DFARS 7012 clause for GCC proper with the publishing of this compliance update.
This means that, if it’s important for you as a DIB contractor to contractually obligate Microsoft to meet the DFARS 7012 clause, including those pesky incident reporting requirements, you can now do so, Microsoft will accept that contractual obligation, and you will remain compliant with sub-paragraphs (c)-(g), which is just as important if not more so.
But again, as I mentioned above, please ensure that GCC is the right set of services for your circumstances. If you intend to store or transmit ITAR/EAR data with Microsoft 365, it’s likely best to keep the data in the US to meet your regulatory obligations. If you don’t plan to comingle your sensitive data with Microsoft 365, it would be prudent to have the administrative and/or technical means to manage incidents for if and when these types of regulated data end up on services that are not authorized to store-process-transmit those data types. Your accreditation boundaries in your System Security Plan should be pretty clear on this.
Microsoft 365 Commercial
Observation 3: Acceptable for Federal Contract Information!
Federal Contract Information (FCI) has a wider industry footprint than it’s CUI/CDI/ITAR cousins and has a much smaller set of protection requirements.
Federal contract information means information, not intended for public release, that is provided by or generated for the Government under a contract to develop or deliver a product or service to the Government, but not including information provided by the Government to the public (such as on public websites) or simple transactional information, such as necessary to process payments.
My interpretation of this is, if you have information provided by or generated for the government in your work, and it’s not marked or identified as being publicly releasable, it’s safe to assume you have FCI.
With that said, if you are confident that you don’t have the more sensitive subsets of FCI that I mentioned earlier – No DFARS 7012 Clause, No ITAR/EAR requirements – but you still do business with the DOD, the security controls of Microsoft 365 commercial should be adequate to meet the 15 basic protection requirements listed in FAR 52.204-21 for FCI. This is now clearly illustrated in Microsoft’s compliance update.
In Conclusion
Moving to Microsoft 365, GCC, GCC High is not inexpensive or without effort. Many of CyberSheath’s customers are taking an approach to minimize the use of these services by establishing enclaves of GCC or GCC High services, accessible only to users who need to work on sensitive data sets – sometimes even establishing these enclaves as an insurance policy for if and when they need to work on CUI or ITAR controlled information. These are viable options for those in the DIB where defense work is only a small fraction of their business, and CUI can easily be identified and controlled. Alternatively, some customers are establishing controls to keep CUI away from their cloud services and owning the compliance burden with on-premises resources and services. Both can be done.
The fact of the matter is the industry is operating under overlapping regulatory guidelines, some of which are interim guidelines, many of which are unfolding before us. It’s great to see Microsoft’s stance on this moving target and providing substantial and informative guidance to assist in decision making related to their services.
CyberSheath is a Microsoft CSP, Microsoft Silver Partner and Microsoft Intelligent Security Association (MISA) member and CMMC AB Registered Provider Organization. Our team has been working with the DOD on DFARS related issues since 2008, initially as a part of the Defense Industrial Base Cyber Security Initiative (DIBCSI).
With hundreds of NIST SP 800-171 assessments and implementations successfully performed for DOD contractors, we can help you cut through the confusion and deliver measurable, ongoing compliance as the Cybersecurity Maturity Model Certification (CMMC) is implemented. For more information, contact a CyberSheath expert today.