The US government, through the lead agency, the Department of Defense (DOD) is implementing a new Cybersecurity Maturity Model Certification (CMMC) requirement for all private-sector businesses that work with the DOD, and now we understand that the standard will be integrated into the GSA and DHS agencies too. However, the standard isn’t exclusive to the US government, and is largely being rolled out through a private-public partnership and can be extended to any company, country, independent of the requirements to use the standard for specific US agencies.
In addition to these agencies, on May 15, 2019, then President Trump issued Executive Order on Securing the Information and Communications Technology and Services Supply Chain (E.O. 13873) to strengthen efforts to prevent foreign adversaries from exploiting vulnerabilities in the ICT supply chain and protect the vast amount of sensitive information being stored in and communicated through ICT products and services.
The E.O. sets out the procedures the Department of Commerce will use to prohibit the use or transaction of “information and communications technology or services designed, developed, manufactured, or supplied by persons owned by, controlled by, or subject to the jurisdiction or direction of a foreign adversary”, and that pose risk of sabotage or subversion; 2) catastrophic effects on the Nation’s critical infrastructure or digital economy; or 3) adverse consequences to national security and public safety.
These new research efforts and the new CMMC requirements will directly affect the roughly 350,000 businesses that are part of the DOD supply chain and now 11 million businesses as part of the GSA and likely spread throughout the entire US government. This new standard’s ripple effect is expected to be even larger, potentially replacing almost all other broadly recognized cybersecurity standards.
The CMMC is a set of security controls being developed under the DOD’s guidance in coordination with industry and academia, building on previous standards including NIST 800-171, 800-53, CSF, ISO 27002, CIS v7, Secure Controls Framework, and others.
Five Reasons ISO 27001/27002 Will Not Last Against CMMC Dominance
Reason One: CMMC is required for contracts with the US government and, the CMMC standard is US law/regulation (e.g. compulsory requirement for covered entities).
- By law, all DOD suppliers must comply with CMMC and increasingly most GSA and DHS suppliers as of this article’s writing. This is a sweeping change. It doesn’t matter if you handle classified information or Controlled Unclassified Information (CUI). If you work with the DOD, supply a DOD prime contractor, or are a supplier to a DOD sub-contractor, this applies to you.
- The federal government is the single largest buyer globally, with annual spending on goods and services close to $450 billion a year. In addition, as estimated US military spending is $934 billion and the Department of Homeland Security (DHS) is $60 billion. Said simply, most of this nearly $1.5 trillion spending will require oversight or CMMC certification by Oct 1st, 2025. How does this compare? There is no other cybersecurity standard globally, which requires certification before their resident business can earn revenue. In other words, CMMC is a VERY different standard in that it directly impacts the underlying revenue of a company.
Reason Two: CMMC is a standard above all standards.
This new standard, driven by the US government’s regulatory might, is likely to become the de facto cybersecurity framework for all businesses—regardless of whether they work with the DOD. The resulting simplification in approach and achievement supply-chain risk will render nearly all other cybersecurity benchmark standards obsolete.
Organizations choose to comply with an information security standard for only one reason: it makes good business sense. Sometimes there are external drivers, such as a key client’s demand, and sometimes the driver is internal, such as a clearly articulated enterprise risk management program.
However, organizations loathe complying with more than one security standard as inefficient and unnecessary.
Some of the factors that go into picking a standard to adopt include:
- Comprehensive. Ability to be applied across a large swath of business types, sizes, geographies, and needs.
- Legal & Reputable. National standards (like NIST) and international (like ISO) organizations have strong reputations and are well-recognized. Virtually all reputable standards address the same topics in their unique way. All businesses do the mapping of one standard to another, so a company that worked on becoming ISO 27001 compliant can explain how it is also NIST 800-53 compliant.
- Applicable. For instance, PCI is relevant to organizations handling payment-card information, and HIPAA is relevant to US Healthcare organizations. The NIST 800-171 is intended for organizations doing business with the US DOD.
- Cost-effective. The organization must be able to achieve and maintain compliance without wrecking the business.
The CMMC ticks all these boxes for about +/- 350,000 DOD companies and a growing list of companies outside of those directly in coverage. Since the CMMC is based on the best of all the current reputable standards, there is no particular need to show how it maps back to them; for most of these companies, there is no compelling business reason to comply with any other standard. Because companies must be certified by an impartial, external third party, the CMMC also provides a much stronger assurance to non-DOD business partners than unsubstantiated claims of being compliant with any other standard. The cost of gaining and retaining compliance is minimal to ensure that the supply chain is secured rather than disrupted.
Also, as organizations earn certification, their CMMC level will drive out other claims about cybersecurity. The CMMC level will also simplify the interactions between businesses regarding how information is protected. Currently, mature organizations include some level of cyber due diligence in their contracting processes. With this new standard, instead of subjecting business partners to long questionnaires about their internal cybersecurity, even non-DOD organizations will only have to ask each other a straightforward question: What is your CMMC level?
Reason Three: Programmatically, CMMC auditors are better than any other auditors in the security space.
Auditors must endure and certify both knowledge, competency, ethics, and security background checks and have the quality of their reviews checked and evaluated. Until now, only the PCI-Standard, the ISO 27001/27002, and HITRUST frameworks offered the option to be certified by a third party. Organizations could say they were compliant, satisfying most who had an interest in security but glossing over that they were not certified. CMMC will require certification by a third party. However, these auditors are very different than ISO in that ethical guidelines bind them, security background checks, knowledge qualification reviews, and qualification checks. The PCI standard is similar in this approach; however, PCI is self-governance from industry versus a legal requirement for all gaining certification. Moreover, CMMC will police the marketing, attestations, and behavior of those participating in a way that should vet frequent offenders.
Reason Four: CMMC is revenue-focused, not policing-focused.
Up until now, NO cybersecurity standard stood in front of a contract et large. CMMC is the only standard in which you may not move forward for fulfillment if you do not certify to the level called for by the desirable contract award. Said another way, you must FIRST become certified not claim ignorance and deny knowledge of one’s responsibility when faced with a policing action afterward.
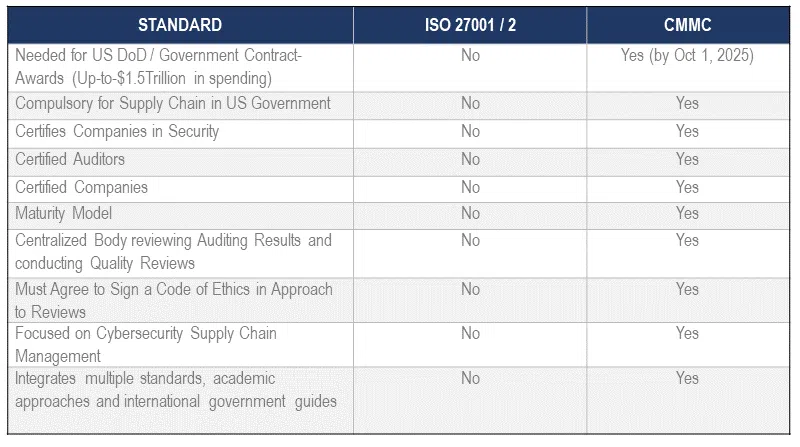
Reason Five: Most companies will need to be CMMC certified; ISO offers nothing more comprehensive.
Review these considerations below:
Say Hello to CMMC and Goodbye to ISO 27001
Overall, the CMMC process only became law in September 2020 and set in motion a five-year transition plan. It’s hard to determine the full impact of this new compliance approach now; however, CMMC will be the de facto standard to build around for a generation or two at the least. Also, the DOD is willing and able to enforce these standards as 2021 has ushered in a whole new class of contract award refusals and business-process changes built around cybersecurity compliance certifications.
It also means that DOD contractors should start taking proactive steps to strengthen their security measures and consider migrating from old standards such as ISO 27001/27002 to CMMC. Consider the maturity level you’ll need to earn to continue to justify your security program’s performance (or your DOD contracts) or make the types of contracts you want to hold in the future.
NIST and CMMC will work hand in hand to make for a safer and more structurally sound data security landscape and supply chain and in its place will be a legion of old standards whose usefulness has sunsetted.