The US Department of Defense (DOD) has one of the largest supply chains in the world, scaling to hundreds of thousands of different vendors and partners. While valuable, these vital partners in our nation’s defense infrastructure pose a huge cyber risk. Today that risk is largely unchecked and unregulated as contractors can “self-attest” to their ability to protect Controlled Unclassified Information (CUI).
Commercial companies are the lifeblood of any economy and the circulatory system of modern day societies. They provide needed innovation, new discoveries, critical high-value support as well as materials and quick solutions to a myriad of problems. From the most arcane to the most mundane, the US Defense Department has needs in nearly every aspect of procuring commercial services, but this lifeblood paradoxically may imperil the entire system by leveraging companies with little respect for cybersecurity controls. In fact, in this connected world, no government or company can perfectly protect all its data from hackers and rival states. Even so, it is astonishing that, from January 2016 to February 2018, nearly 6 percent of U.S. military and aerospace contractors reported data breaches (according to Stars & Stripes).
And experts feel this is just the tip of the iceberg – the vast majority of security incidents are never uncovered. The Pentagon needs to tighten cybersecurity across its vast contracting operations and hold contractors accountable for minimum standards of care around cybersecurity. Essentially that is the goal behind the Cybersecurity Maturity Model Certification (CMMC) and the ambitious effort to secure the DOD supply chain. The CMMC effort is not without its critics but who can argue that real change wasn’t urgently needed? Learn More about CMMC
Let us review some major breaches of national security that hopefully can be prevented in a post CMMC world so that you might be the judge:
Example One – Jan-Feb, 2018: Comprise of US Navy “Operation SEA DRAGON” – Chinese hackers stole sensitive U.S. Navy submarine plans from Rhode Island DOD contractor
Citing unnamed U.S. officials, the Washington Post reported in June of 2018 about a very disturbing cyberattack of a US DOD contractor. Evidently Chinese government hackers compromised the computers of a U.S. Navy contractor and stole a large amount (approximately 600+ Gigabits) of highly sensitive data on undersea warfare, including plans for a supersonic anti-ship missile for use on U.S. submarines.
The breaches took place in January and February, the officials told the Post, speaking on condition of anonymity about an ongoing investigation led by the Navy and assisted by the Federal Bureau of Investigation.
The U.S. Navy and an unnamed defense contractor are/were working on a new missile which the Navy says will give its submarines a new, “disruptive offensive capability” to take on enemy ships. The previously unknown weapon, known as Sea Dragon, supposedly combines an existing U.S. Navy platform with an existing capability, is likely a new version of a versatile air defense missile capable of pinch-hitting as an anti-ship missile.
Example Two – March 2019: US Navy Review Concludes it is “Under Siege” by Chinese Hackers & Attackers
An internal U.S. Navy review concluded that the service and its various industry partners are “under cyber siege” from Chinese hackers who are building Beijing’s military capabilities while eroding the U.S.’s advantage, The Wall Street Journal reported Dec 2018 – Mar 2019. Chinese hackers have repeatedly hit the Navy, defense contractors, and even universities that partner with the service. “We are under siege,” a senior Navy official told The Journal. “People think it’s much like a deadly virus — if we don’t do anything, we could die.”
Three particularly worrisome recent incidents (2018-2020) were the theft by China of highly sensitive information on naval projects left on an unclassified network (2019), last year’s breach of private information on 30,000 Pentagon employees(2018), and the exposure of 60,000 files on a publicly accessible server involving a subcontractor to Booz Allen Hamilton (2018), the firm that employed Edward Snowden. And perhaps most embarrassing was the 2016 theft of sensitive plans for the F-35 fighter — a plane that will cost taxpayers $1.5 trillion over its lifespan. A small Australian subcontractor on the project had reportedly never changed its Windows passwords from the defaults “admin” and “guest.”
Example Three – Sept-Dec 2019: Compromise of Emails and LinkedIn Accounts of military defense companies
In a report released in June 2020 by Slovakia-headquartered ESET cybersecurity company who said the cyberattacks of mainly European aerospace and military defense firms were launched between September and December 2019. A collaborative investigation with two of the affected European companies allowed them to gain insight into the operation and uncover previously undocumented malware.
To compromise their targets, the attackers used social engineering via LinkedIn, hiding behind the ruse of attractive, but bogus, job offers. Having established an initial foothold, the attackers deployed their custom, multistage malware, along with modified open-source tools. Besides malware, the adversaries made use of living off the land tactics, abusing legitimate tools and OS functions. Several techniques were used to avoid detection, including code signing, regular malware recompilation, and impersonating legitimate software and companies.
According to their investigation, the primary goal of the operation was espionage. However, in one of the cases we investigated, the attackers attempted to monetize access to a victim’s email account through a business email compromise (BEC) attack as the final stage of the operation.
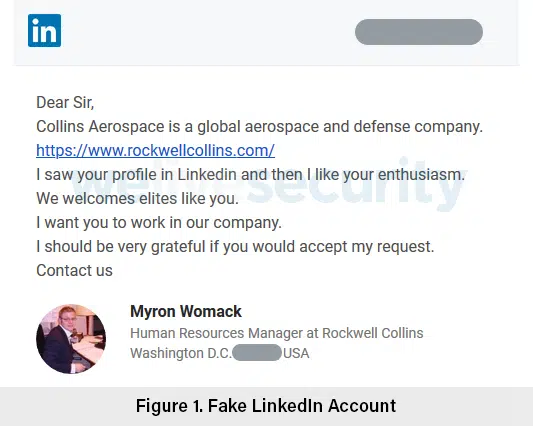
As part of the initial compromise phase, the Operation In(ter)ception attackers had created fake LinkedIn accounts posing as HR representative of well-known companies in the aerospace and defense industries. In our investigation, we’ve seen profiles impersonating Collins Aerospace (formerly Rockwell Collins) and General Dynamics, both major US corporations in the field.
With the profiles set up, the attackers sought out employees of the targeted companies and messaged them with fictitious job offers using LinkedIn’s messaging feature, as seen in Figure 1. (Note: The fake LinkedIn accounts no longer exist.)
Once the attackers had the targets’ attention, they snuck malicious files into the conversation, disguised as documents related to the job offer in question.
Example Four – 2017-2020: The Chinese APT Threat to Cleared Defense Contractors
In a report published in June of 2020, cyber-security firm Lookout said it found evidence connecting Android malware (APT 15) that was used to spy on minorities in China to a large government defense contractor from the city of Xi’an.
Lookout’s 52-page report details a years-long hacking campaign that has primarily targeted the Uyghur ethnic minority, living in western China, but also the Tibetan community, to a lesser degree.
The campaign infected individuals in these communities with malware, allowing government hackers to keep an eye on the activities of minority communities in China’s border regions but also living abroad in at least 14 other countries.
“Activity of these surveillance campaigns has been observed as far back as 2013,” Lookout researchers said. The company attributed this secret surveillance to a hacking group they believe operates on behalf of the Chinese government.
The fact that Lookout linked an APT15 malware sample to a Chinese defense contractor is not a novel discovery. From 2017 to 2019, four other Chinese state-sponsored hacking groups have been linked to contractors hired by Chinese intelligence agencies operating in various regional offices.
This includes:
APT3 – linked to a company named Boyusec operating on behalf of Chinese state security officials in the province of Guangdong
APT10 – linked to several companies operating on behalf of Chinese state security officials in the province of Tianjin
NEW! APT 10 – Xi’an Tianhe Defense Technology, a large defense contractor in the city of Xi’an, in central China.
APT17 – linked to several companies operating on behalf of Chinese state security officials in the province of Jinan
APT40 – linked to several shell companies operating on behalf of Chinese state security officials in the province of Hainan
Operators behind APT3 and APT10 have eventually been charged by the US Department of Justice in November 2017 and December 2018, respectively.
Based on previous threat intelligence reports published by cyber-security firms Recorded Future and CrowdStrike, the Chinese Ministry of State Security outsources hacking operations to outside contractors, who report directly to, and take orders from intelligence officials.
An FBI warning in 2018 specifically cites examples against “Cleared Defense Contractors” and here is an excerpt of the alert:
“APT actors in the near future likely intend to target US Cleared Defense Contractors (CDC) via spear phishing campaigns or network infrastructure compromises, according to recent intelligence. Common spear phish targets may include individuals featured on internet-facing CDC Web sites and high-ranking CDC executives.
FBI has observed APT actors over the past two years precede spear phishing campaigns with open source research of targeted US company websites, particularly sections containing contact information for company officials which include names, titles, telephone numbers, and email addresses. In one case, an APT actor sent spear phishing emails within one-to-two weeks after researching the targeted US company.
Historically, APT actors have a strong desire to collect US defense and scientific intelligence to further their interests and advance strategic goals. As a result, US CDCs and research facilities may likely be targets for cyber adversaries due to their involvement in national security and their close relationship with the US Government.”
Example Five – Feb-June 2020: DCSA Bulletin – US Defense Focused
In a report published recently by politico, they suggest they obtained a Defense Counterintelligence and Security Agency (DCSA) bulletin marked “unclassified/for official use only” and warns that DCSA’s cyber division detected nearly 600 “inbound and outbound connections” from “highly likely Electric Panda cyber threat actors” targeting 38 cleared contractor facilities, including those specializing in health care technology. Moreover, the bulletin goes on to say, “Nearly 40 U.S. contracting facilities with access to classified information have been targeted by a hacking group with suspected ties to the Chinese government since Feb. 1”, according to a bulletin disseminated to contractors by the Defense Counterintelligence and Security Agency.
The so-called Electric Panda group is not new and appears to have been operating since at least 2016, according to one of the indicators listed by DCSA. The bulletin goes on to say that this group has been targeting contractors that specialize in cybersecurity, aerospace, naval, health care, power generation, IT systems, telecommunications, risk analysis, and space systems.
Conclusions: How to Solve the Problem?
Given this, how safe is the US DOD Supply chain from cyberattacks? From casual, publicly available information, there is strong evidence that the supply chain base of the US DOD system is under dedicated and constant attack, most probably needs dramatic investments in order to stay safe and sound from cyberattacks and to keep the US military safe.
The key to understanding the solution is to understand that the threat is immeasurably more serious as we must concern ourselves with the great possibility of a loss of life scenarios.
Let us hope that the new CMMC regulation is a very important step in accelerating the awareness of the real possibilities of these dangers, then to assemble a well-orchestrated cybersecurity risk and mitigation strategy for each attribute of DOD Supply chain may be placed in harm’s way.
Next Steps
If you have any questions or would like support as you ready your organization for CMMC, contact us. We also invite you to listen to Eric Noonan, CyberSheath CEO, in a recorded webinar to learn how to start preparing your organization for CMMC by leveraging the steps you have taken to be compliant under DFARS. Register Now
In this webinar you will learn:
- Mapping NIST 800-171 to CMMC
- Levels 1-5: Challenges and complexities to consider at each compliance level
- Step by step path to attaining CMMC