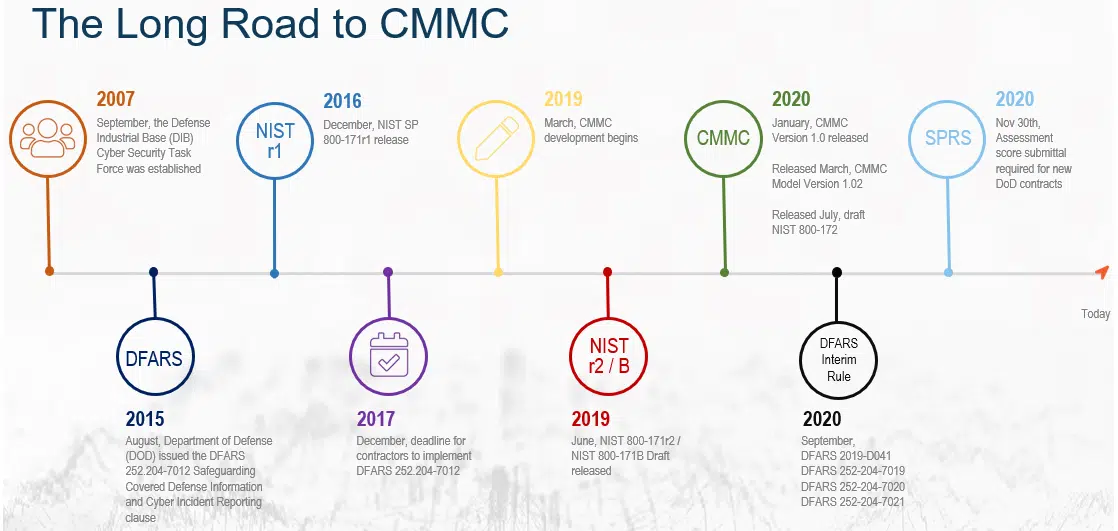
The SolarWinds hack and the subsequent Senate hearings attended by principal players in that event have made supply chain cybersecurity a national discussion. Some of the questions being asked suggest that America is for the first time considering how to protect our supply chains, form effective public/private partnerships, share cyber threat intelligence and enforce mandatory breach disclosure among a relevant group of stakeholders. However, it is not the first time; many parts of the federal government have been working hard to answer these questions with considerable progress for a long time. Specifically, I can speak from my nearly thirteen-years of experience and the progress I have witnessed firsthand between the Department of Defense (DOD) and the Defense Industrial Base (DIB).
A Public/Private Partnership
The public/private partnership between the Department of Defense, the largest procurement authority in the world, and its supply chain has substantially answered nearly every salient question being asked in the wake of the SolarWinds breach. The partnership has spanned four presidential administrations and gained a decade of bipartisan support. The parties have operationalized threat information sharing, breach disclosure, and mandatory minimums for supply chain cybersecurity. Some of the very people I worked with more than a decade ago when the DOD, Intelligence Community and Industry came together for the first time are now leading the way for the current presidential administration. Anne Neuberger, for example, has been appointed to lead the government’s response to the SolarWinds hack for President Biden. Anne has been on the front lines of these issues since at least 2009 when I worked with her as a part of the Defense Industrial Base Cybersecurity initiative (DIBCSI), and she understands the issues inside and out. Anne knows the legal limitations of our intelligence agencies domestically, has heard all of the industry’s concerns and has long been a part of the teams working through these issues.
DIBCSI, initially led many years ago by Victoria Morgan, an unsung heroine who dragged along reluctant defense industry prime contractors, questioning, “who is going to pay for this?,” to a partnership with DOD, has evolved into the Cybersecurity Maturity Model Certification (CMMC). Led by another DOD heroine, Katie Arrington, CMMC has answered the cost question, made the program law, and dramatically increased awareness of the responsibilities that come with being a defense contractor. Defense contractors have had a seat at the table for more than a decade in this partnership and have helped DOD and the federal government answer many of the questions being posed in the wake of the SolarWinds breach.
Let’s look at the critical questions being asked and the answers that the DOD and their supply chain have collectively crafted throughout the decade-plus partnership.
Threat Information Sharing and Breach Disclosure
The DOD and industry partnership produced DFARS clause 252.204-7012 Safeguarding Covered Defense Information and Cyber Incident Reporting, which mandates rapid reporting of cyber incidents to DOD. Specifically, the clause requires:
(c) Cyber incident reporting requirement.
(1) When the Contractor discovers a cyber incident that affects a covered contractor information system or the covered defense information residing therein, or that affects the contractor’s ability to perform the requirements of the contract that are designated as operationally critical support and identified in the contract, the Contractor shall—
(i) Conduct a review for evidence of compromise of covered defense information, including, but not limited to, identifying compromised computers, servers, specific data, and user accounts. This review shall also include analyzing covered contractor information system(s) that were part of the cyber incident, as well as other information systems on the Contractor’s network(s), that may have been accessed as a result of the incident in order to identify compromised covered defense information, or that affect the Contractor’s ability to provide operationally critical support; and
(ii) Rapidly report cyber incidents to DOD.
(2) Cyber incident report. The cyber incident report shall be treated as information created by or for DOD and shall include, at a minimum, the required elements.
(3) Medium assurance certificate requirement. In order to report cyber incidents in accordance with this clause, the Contractor or subcontractor shall have or acquire a DOD-approved medium assurance certificate to report cyber incidents.
(d) Malicious software. When the Contractor or subcontractors discover and isolate malicious software in connection with a reported cyber incident, submit the malicious software to DOD Cyber Crime Center (DC3) in accordance with instructions provided by DC3 or the Contracting Officer. Do not send the malicious software to the Contracting Officer.
(e) Media preservation and protection. When a Contractor discovers a cyber incident has occurred, the Contractor shall preserve and protect images of all known affected information systems identified in paragraph (c)(1)(i) of this clause and all relevant monitoring/packet capture data for at least 90 days from the submission of the cyber incident report to allow DOD to request the media or decline interest.
(f) Access to additional information or equipment necessary for forensic analysis. Upon request by DOD, the Contractor shall provide DOD with access to additional information or equipment that is necessary to conduct a forensic analysis.
(g) Cyber incident damage assessment activities. If DOD elects to conduct a damage assessment, the Contracting Officer will request that the Contractor provide all of the damage assessment information gathered in accordance with paragraph (e) of this clause.
CMMC: A Framework that has Considered and Solved Legal, Logistical, and Operational Issues
Looking at this list of reporting requirements, we have a framework that has considered and solved many legal, logistical, and operational issues around threat information sharing and breach disclosure. Many elements of the law have been in place for almost six years now, with some having been implemented voluntarily for more than a decade. It changes the behavior of the largest supply chain in the world and was created to answer many of the questions currently being asked before important government bodies.