As you are probably aware, there is a new mandatory certification model that will be required to do business with the Department of Defense (DOD). The CMMC (Cybersecurity Maturity Model Certification) builds on best practices established in NIST 800-171 (DFARS), NIST 800-53, ISO 27001, ISO 27032, AIA NAS9933, and others, to create one unified standard for cybersecurity.
CMMC will be a dynamic standard, growing and evolving with the demands of the ever-changing cybersecurity landscape. While the structure of CMMC is set, the details of the new standard are still being vetted, refined, and finalized. The target for launch is early 2020.
How CMMC Compares to NIST 800-171
Similarities
The purpose of both standards is to ensure that DOD contractors employ healthy cybersecurity practices to protect sensitive information. There are several facets of security posture that must be met in order to be in compliance with both standards. Both also require demonstrated compliance to do business with DOD, via self-certification for DFARS and via an audit by certifying organization for CMMC.
Differences
One important distinction touched on above is that CMMC will not allow self-certification. Compliance with the standard will be verified by an outside third-party hired by your company to determine your compliance with the requirements.
The CMMC control framework is (currently) much larger than the 14 control families and 110 controls outlined in NIST 800-171, highlighting the importance of thorough CMMC standard preparation. As of October 31, 2019, CMMC contains 18 domains, 241 practices, and 90 processes at Maturity Level 3.
CMMC Components
The elements of CMMC include:
- Maturity Levels – These levels range from basic security controls required for level 1 through highly advanced requirements for level 5.
- Domains – Based on cybersecurity best practices, these are key sets of capabilities for cybersecurity, such as Access Control, Incident Response, Security Assessment, and more.
- Capabilities – These achievements are the building blocks of each domain, ensuring cybersecurity within each domain.
- Practices – These are individual cybersecurity activities related to NIST “controls”. They range from Level 1 practices including anti-virus and ad hoc cybersecurity governance to Level 5 practices such as real-time asset tracking and device authentication.
- Processes – These are documented standards for implementing practices based on the maturity level of your organization.
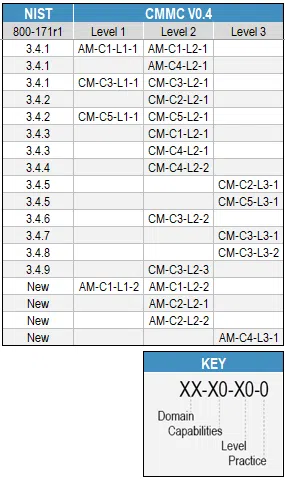
Below is an example of a cross-reference matrix between NIST and CMMC draft 0.4. It shows some interesting characteristics, such as:
– One NIST Family mapping to multiple CMMC Domains
– One NIST control mapping to multiple CMMC Levels
– One NIST control mapping to multiple CMMC Capabilities
– One NIST control mapping to multiple CMMC Practices
– New CMMC practices not found in the NIST controls
Note, as with most mappings of this kind, they are not always clean, with some aspects of a Control in one framework mapping to elements of a Practice in a different framework.
What You Can Do Now
CMMC specifically calls out the requirement for documentation for all domains in order to achieve compliance. Note that this condition was never explicitly requested in NIST 800-171; rather it is noted in the DFARS appendix that it was assumed you had the appropriate documentation.
While CMMC is continuing to evolve, you can ready your organization to meet the requirements of the new standard. Achieving CMMC compliance will not be a quick endeavor as you will need to define and record your real working processes.
Start now by cataloging your processes and building out the documentation that is called out in NIST as this will surely aid your CMMC compliance activities.
CMMC Maturity Levels 2, 3, 4, and 5 will require Policy, Process, and Plan documents. According to NIST, here are the plans you should have in place:
- Business Continuity Plans
- Contingency Plans
- Continuity of Operations Plans
- Critical Infrastructure Plans
- Crisis Communications Plan
- Disaster Recovery Plans
- Incident Response Plan
- Incident Response Testing Plan
- Occupant Emergency Plan
- Physical/Environmental Protection Plan
- Plan of Action
- Security Assessment Plan
- Security Plan
- System Security Plan
And here are the policies and procedure you should have as well:
- Access Control
- Audit and Accountability
- Configuration Management
- Configuration Planning
- Incident Response
- Identification and Authentication
- Information Flow Control
- Information Flow Enforcement
- Information System Maintenance
- Media Protection
- Media Sanitation and Disposal
- Mobile Code Implementation
- Password
- Personnel Security
- Physical and Environmental Protection
- Portable Media
- Risk Assessment
- Security Assessment and Authorization
- Security Awareness and Training
- Security Planning
- Separation of Duties
- System and Information Integrity
- System and Services Acquisition
- System and Communication Protection
- System Use
Prepare yourself by understanding the latest CMMC updates and, more importantly, how your business should respond to achieve documented, audit-proof evidence of compliance. Listen to Eric Noonan, CyberSheath CEO, in this recorded webinar as he explains how to cut through the noise and jump-start your DFARS compliance efforts. No matter where you are in your journey towards NIST 800-171 compliance this webinar is guaranteed to better equip you in understanding, implementing, and maintaining compliance!
Register Now to gain your access to the webinar. If you have any questions or would like support as you ready your organization for CMMC, contact us.

