The theft of intellectual property and sensitive information across the Defense Industrial Base (DIB) and the supply chain of the Department of Defense (DOD) threatens economic security and national security. Malicious cyber actors have persistently targeted the DIB sector and the DOD supply chain resulting in loss of intellectual property and unclassified information, which threatens U.S. technical advantages and significantly increase risks to national security.
The DOD is taking action to combat these threats. CMMC maturity levels will soon be used to determine whether a company will or will not be awarded a contract. To state that a different way: There are new regulatory cybersecurity minimums that must be validated by an independent third party prior to contract award on Defense Contractor networks.
What is CMMC?
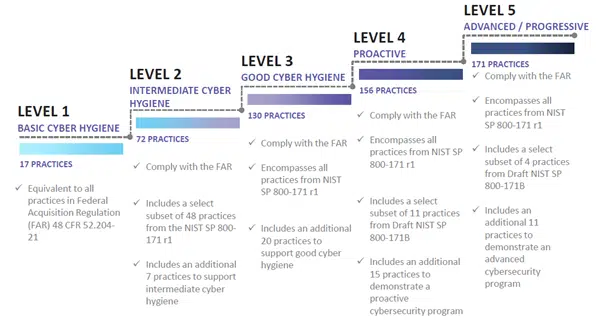
CMMC encompasses multiple maturity levels that range from “Basic Cybersecurity Hygiene” to “Advanced/Progressive”. The evolving certification is focused on the protection of unclassified information across the supply chain categorized as:
- Federal Contract Information (FCI): FCI is information provided by or generated for the Government under contract and not intended for public release.
- Controlled Unclassified Information (CUI): CUI is information that requires safeguarding or dissemination controls pursuant to and consistent with laws, regulations, and government-wide policies, excluding information that is classified under Executive Order 13526, Classified National Security Information, December 29, 2009, or any predecessor or successor order, or the Atomic Energy Act of 1954 as amended.
The CMMC model consists of five maturity levels and 171 cybersecurity practices mapped across these maturity levels. This structure helps to institutionalize cybersecurity activities, ensuring that they are consistent, repeatable, and of high quality. The CMMC practices provide a range of mitigation across the levels, starting with basic safeguarding at Level 1, moving to the broad protection of Controlled Unclassified Information (CUI) at Level 3, and culminating with reducing the risk from Advanced Persistent Threats (APTs) at Levels 4 and 5.
The CMMC framework is coupled with a certification program to verify the implementation of these important cybersecurity processes and practices.
Is CMMC different from DFARS Clause 252.204-7012 and NIST 800-171?
Yes. While the requirement for DFARS Clause 252.204-7012 Safeguarding Covered Defense Information and Cyber Incident Reporting has been mandatory for several years, enforcement has been inconsistent and self-certification has been allowed, until now. CMMC changes that. Defense Contractors must now implement mandatory minimum levels of cybersecurity prior to contract award. They must also have their implementation of cybersecurity controls validated by a third party. Self-certification is no longer allowable.
The majority of CMMC practices (110 of 171) originate from the safeguarding and security requirements specified in FAR Clause 52.204-21 and DFARS Clause 252.204-7012. It is expected that the vast majority of defense contractors will need to be certified at CMMC Maturity Level 1 or 3.
- Level 1 is equivalent to all of the safeguarding requirements from FAR Clause 52.204-21.
- Level 3, building on Levels 1 and 2, includes all of the security requirements in NIST 800-171 plus other practices.
While the actual CMMC certification process is still a work in progress, defense contractors that implement the 110 security requirements of NIST 800-171 will have a head start towards achieving compliance with the new certification once it takes effect. In fact, CMMC Maturity Level 3 includes all 110 NIST 800-171 security requirements, making 85% of Maturity Level 3 compliance based on NIST 800-171 compliance.
The DOD is building on and strengthening, not abandoning, NIST 800-171. While specific maturity levels for individual contracts have not yet been determined, it is understood that implementing NIST 800-171 security requirements is the best way to prepare for CMMC. Get to work implementing NIST 800-171 to put yourself in a position to succeed.
How will CMMC affect the Acquisition Process?
CMMC will have a dramatic impact. Self-certification is being replaced with third party validation prior to the contract award. Checkbox compliance with nothing more than the documentation of a System Security Plan (SSP) and Plans of Action & Milestones (POA&Ms) is no longer sufficient. Doing business with the DOD now means a commitment to cybersecurity that is based on trust but verify DOD process for all 300,000 plus DOD suppliers.
How can I get ready for CMMC?
Given that the DOD has made NIST 800-171 the foundation for certification, preparing for CMMC is a relatively straightforward process. While not easy or free, it is uncomplicated to determine the steps necessary, timing, and priority. Here are measures to take to get started.
- Step 1. Assess your current operations for compliance with NIST 800-171.
- Step 2. Document your System Security Plan (SSP).
- Step 3. Document your Plan of Actions & Milestones (POAMs).
- Step 4. Implement the required controls.
- Step 5. Maintain compliance.
For an easy-to-follow guide on how and in what order you should start getting ready for your mandatory third party CMMC audit, download our guide.
Why CyberSheath
There is no better company to help you in doing the actual work required to achieve CMMC compliance. CyberSheath has been working with the DOD and its suppliers for nearly a decade as CMMC has evolved from voluntary to self-certification, and now mandatory third party certification. Our CEO is a former Chief Information Security Officer for one of the largest defense companies in the world, and our employees are all practitioners, not consultants. What is the difference? Consultants just tell you what to do in presentation slides; we know what action to take and we do it.