Background
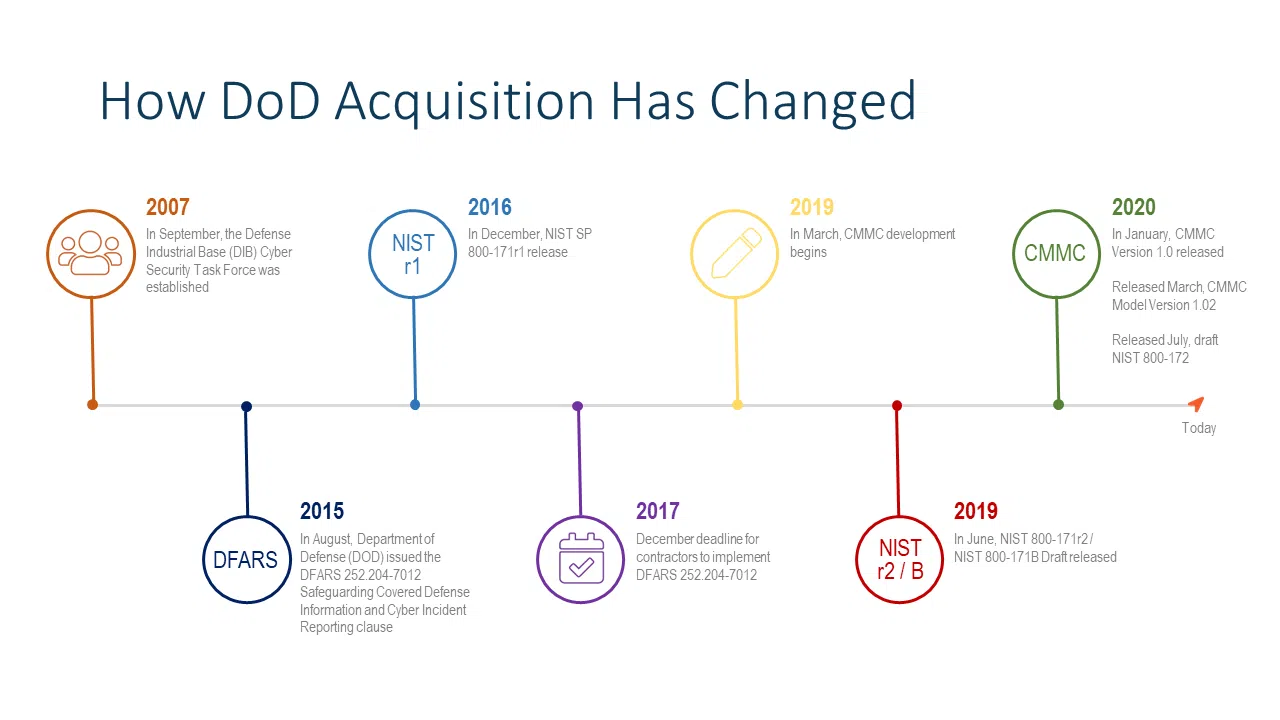
In 2019, the Department of Defense (DOD) officially announced the introduction of a Cybersecurity Maturity Model Certification (CMMC). This unique maturity model is designed to improve the cybersecurity regarding Controlled Unclassified Information (CUI) within supply chains, especially as it applies to the Defense Industrial Base (DIB).
Version 1.0 of the CMMC framework was released in January 2020. By June 2020, CMMC requirements have started to be included in DOD and later GSA Stars Contracts Request for Information (RFIs) and Requests for Proposals (RFPs). Think about that for a second, within six months of creating a new model to assess the cybersecurity of defense contractor networks the language has started appearing in official acquisition documents. The CMMC train has left the station, in a hurry.
CMMC is the latest entry in regulations from a decade long process of public/private partnership between the DOD and DIB. Critically, the DOD is moving away from contractor led self-assessment and reporting to compulsory third-party certification pre-contract award. You will need certification, from an independent third party for future DOD contracts. (See graphic below.)
Who Must Comply?
As of this post, CMMC was still working its way through the rulemaking process for DFARS (Defense Federal Acquisition Regulation Supplement), which is expected to be released in November 2020. That said if your company provides products being sold to the Department of Defense (DOD) you are required to comply with the minimum cybersecurity standards set by the current DFARS clause 252.204-7012. All DOD contractors that process, store, or transmit Controlled Unclassified Information (CUI) must meet DFARS minimum security standards or risk losing their DOD contracts. DFARS provides a set of adequate security controls to safeguard information systems where contractor data resides. Based on NIST Special Publication 800-171 “Protecting Controlled Unclassified Information in Non-Federal Information Systems and Organizations,” manufacturers must implement these security controls through all levels of their supply chain. The silver lining is that CMMC builds on NIST 800-171 so when in doubt that is where you should start as it’s the current legal requirement.
If your DOD contracts do not require you to process, store, or transmit CUI, you must still protect Federal Contract Information (FCI) under Federal Acquisition Regulation (FAR) 52.204-21. Examples of FCI include contract documents, schedules, billing information, etc. The new DFARS clause is expected to combine the cybersecurity requirements from DFARS 25.204-7012 and FAR 52.204-21 into a common framework based on the CMMC model.
Government contractors are now being asked to effectively police their supply chains to address, among other risks, cybersecurity. Supply chain management is now a key element to ensuring a company’s compliance with laws, regulations, and its internal policies, and to identify risks that could impact a company’s ability to perform, as well as its reputation. The fact that supply chains are global, increases the risks and demands on companies.
In fact, they must not simply police their supply chain, but they are legally bound to use specific contract verbiage with providers who may interface with CUI information which is as follows:
DFARS 252.204-7012(m): “Include this clause, including this paragraph (m), in subcontracts, or similar contractual instruments, for operationally critical support, or for which subcontract performance will involve covered defense information,…”
Keypoints to this law:
- All third-party providers (TPPs) and Managed Security Service Providers (MSSPs) must be obligated to DFARS if they house, control, process, or maintain CUI.
- You are not in compliance with CMMC if your downstream MSSPs / TPPs are not compliant.
- You are not compliant if you don’t have contractually compliant language between you and the TPPs / MSSPs.
Navigating the dizzying world of different CMMC solutions can be a daunting task. The recommended solutions and vendor mix can be very hard to understand. Now let’s investigate these key points made above in more detail:
Pivotal question: Does my TPP or MSSP need to be compliant?
All TPPs and MSSPs must be obligated to DFARS if they house, control, process, or maintain CUI. What exactly is CUI? Let’s read on:
I want to repost an excerpt from our key business partner Microsoft in which Richard Wakeman provides a blog on CUI as follows:
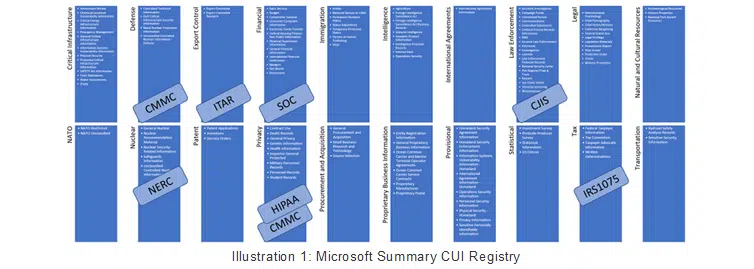
If you have not read the CUI History from the National Archives and Records Administration (NARA), I highly recommend it. It’s a short read, and helpful for context. To summarize, before the advent of CUI, there was a myriad of autonomous Federal agencies and departments that had each developed its own practices for protecting sensitive information. This non-conformity made it extremely difficult to share information with transparency throughout the Federal government and its stakeholders, such as the Defense Industrial Base (DIB). The CUI program is an ever-evolving initiative to standardize the markings and data protection practices across Federal agencies to facilitate sharing of sensitive information, transcending individual agencies. Ultimately, NARA oversees the CUI Program and is primarily scoped to the Federal executive branch agencies. Major contributors to the program include the DOD, the Department of Energy (DoE), the Department of Homeland Security (DHS), the Department of State (DoS), etc. NARA defines CUI as: “Controlled Unclassified Information (CUI) is information that requires safeguarding or dissemination controls pursuant to and consistent with applicable law, regulations, and government-wide policies but is not classified under Executive Order 13526 or the Atomic Energy Act, as amended.”Presidential executive orders evolved to a rule published in 2016 called “32 CFR Part 2002 Controlled Unclassified Information”. You can read about it here in the Federal Register. 32 CFR Part 2002 prescribes the CUI Program markings that span many categories and groupings. The groupings consist of everything from Financial and Privacy data, all the way up to Export Controlled and Intelligence data. Read the CUI Marking List.
3 Key Questions for your MSSP to indicate CMMC Compliance
Question 1: Is the CUI housed in USA Sovereignty? – Or – Where are the location of all operations? Perhaps another way to ask this question is by querying if the vendor has any operations located outside of the US?
A key attribute to the US DOD supply chain is understanding where their supply chain is located, and whether the location may provide some risk to the DOD supply chain. U.S. companies that do business abroad or handle overseas data will now have to comply with a host of new cybersecurity rules after China became the latest country to impose regulations on firms operating there.
This follows hot on the heels of the Clarifying Lawful Overseas Use of Data (CLOUD) Act, which came into force in the U.S. in March 2018, and the European Union’s (EU) General Data Protection Regulation (GDPR), introduced two months later.
The implementation of these new protocols is driven by the recent surge in cyberattacks and, in the case of China, greater protectionism, exacerbated by the U.S. trade war, as the world becomes more divided. Regardless, there are many cybersecurity firms that maintain global operations and software maintenance stations in unassuming regions of the world and this must be understood before you select your vendor.
Question 2: Like Amazon Web Services, Microsoft and Google, do you separate out your government CUI customers from the infrastructure of all of your other customers? Does your provider know how to make the infrastructure comply with the various forms of CUI?
Here is the issue with mixed tenants of cloud environments and the protection of CUI which was quoted by Microsoft’s blog:
“Microsoft has prescribed the US Sovereign Cloud with Azure Government and Microsoft 365 GCC High to protect CUI and CDI consistently. Our rationale is that CUI does include ITAR regulated data, and the DOD requires DFARS 7012 to protect it. We only accommodate that contractually across Azure, Office 365, and Dynamics 365 in the US Sovereign Cloud. It’s that simple. It’s true that you may demonstrate compliance for CUI in our Commercial or GCC cloud offerings, but you will not get a contractual obligation from Microsoft to protect an aggregate of CUI anywhere else other than in the US Sovereign Cloud. It will be your sole responsibility to prove and maintain compliance for it in other clouds.”
Question 3: Have you placed the DFARs compliant verbiage on CUI into the contract with the MSSP / TPP? Was this a standard offering in verbiage in their contracts or non-standard?
I believe this is self-explanatory however to make this point very poignant let’s look at the prescribing law:

For many organizations, their technology, and the corresponding data are among their most valued assets. An organization’s CMMC / CUI Cybersecurity Program is an ever-evolving initiative that attempts to standardize the security data protection practices across supply chains including third-party providers and managed security service providers. If your TPP or MSSP cannot meet the full requirements of CMMC certification, it is unlikely that you will be able to successfully complete a CMMC certification assessment. When choosing TPP’s or MSSP’s, choose wisely, your DOD revenue may depend on it.
Looking for an MSSP to partner with on your journey to CMMC preparation?
Join CyberSheath’s Eric Noonan, CEO, and Carl Herberger, VP of Security Services, dive into CyberSheath’s CMMC Managed Services for Defense Contractors using Microsoft Technology Stack during our upcoming webinar September 30, 2020, at 9:00 am | 12:00 pm EST > Access Replay
