Current Compliance Landscape
Deputy Defense Secretary Patrick Shanahan spoke at the Armed Forces Communications and Electronics Association (AFCEA) on Feb 6, 2018, and said, “The culture we need to get to [around IT security] is that we’re going to defend ourselves and that we want the bar to be so high that it becomes a condition of doing business.” Fast forward two years later and we are on the cusp of one of the largest changes to DOD acquisition ever with mandatory minimums for cybersecurity across all DOD contracts.
For commercial firms providing services to the U.S. defense industry, the challenge that is cybersecurity has been growing for years but largely without any oversight from the DOD. Defense budgets and the use of contractors have grown in parallel to the storing of important, yet unclassified information on commercial defense contractor networks. This exposure, Controlled Unclassified Information (CUI) resident on unregulated and often under secured contractor networks across the DOD supply chain has become a risk that requires addressing for the DOD.
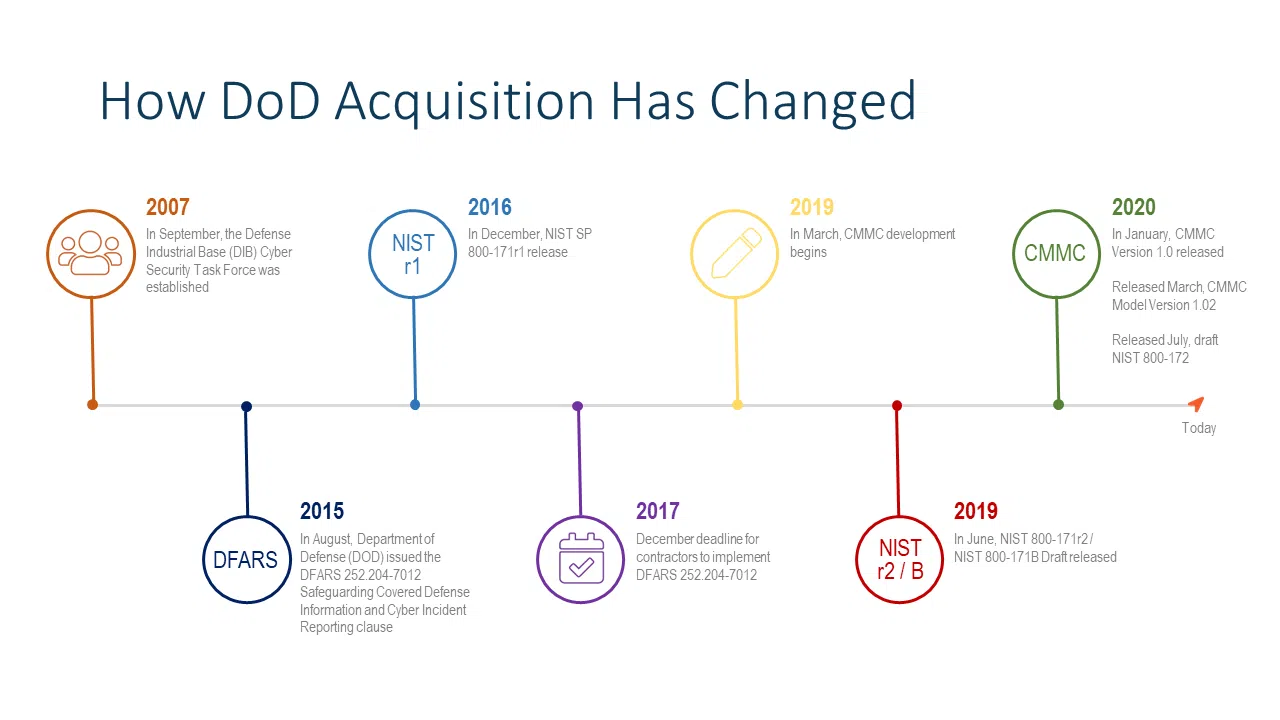
The Defense Industry has always worried about security around products and services. However, the business systems and IT infrastructure that supported those defense contractors were not monitored or significantly regulated by the US Government although vulnerable to attack. The Pentagon has acknowledged an urgent need to tighten cybersecurity across its vast contracting operations and hold contractors accountable for minimum standards of care around cybersecurity. Indeed, the requirements to protect data have been expanding for more than a decade and the Federal Acquisition Regulation (FAR) and the General Services Acquisition Regulation (GSAR) are expected to add data protection requirements in 2020. In truth, the new Cybersecurity Maturity Model Certification (CMMC) and the ambitious effort to secure the DOD supply chain has been underway for many years now (see chart below).
Overview of CMMC
The Cybersecurity Maturity Model Certification (CMMC) program will serve as a method of verifying that appropriate levels of cybersecurity controls and processes meet a specific standard and are in place to protect controlled unclassified information that may be held on the DOD’s industry partners’ networks.
The CMMC program builds on another US government acquisition regulation called DFARS Clause 252.204-7012 which requires the implementation of NIST SP 800-171, Protecting Unclassified Information in Nonfederal Information Systems, and Organizations, as the standard for defense contractors handling CUI data. As such, compliance with NIST 800-171 has been essential for winning and sustaining contracts since 2017 but the lack of oversight and auditing has led to many self-certified contractors that might not stand up to the scrutiny of a 3rd party audit. Because CMMC is at its foundation based on DFARS Clause 252.204-7012 and NIST SP 800-171 it’s important to understand these two separate but related requirements.
CMMC, when finalized and fully mature, will require independent validation of compliance by a CMMC Third-Party Assessor Organization (C3PAO). This is a significant change from DFARS Clause 252.204-7012 which allowed for self-certification and could upend a largely unprepared supply chain that has taken advantage of lax oversight and enforcement.
CMMC is broken down into five compliance levels which a company will need to be certified to be able to be awarded a DOD contract. The levels break down (see below) into demonstrable levels of cybersecurity maturity from which a defense contractor can acquire more and more abilities to conduct services with the DOD.
Your Current Managed Security Service Provider (MSSP) Probably Isn’t Doing Enough For CMMC
Most small business defense contractors do not separate IT from cybersecurity and often the IT work takes priority, not cybersecurity or compliance. Small businesses with one or two IT staff members who are already oversubscribed have no chance of ingesting CMMC and achieving compliance without the help of a Managed CMMC Service. Maintaining the security and compliance programs required by the government is now a full-time job and failure to do so will prevent your company from doing business with the DOD. No matter how qualified or knowledgeable, a small team simply does not have time or the breadth of skills to architect, administer, and manage their environments in alignment with CMMC requirements. You cannot do it alone.
Over the last decade, many businesses have outsourced their security and/or compliance requirements through a Managed Security Service Provider (MSSP). Effectively MSSPs take care of the security requirements and allow a business to focus on their core competencies. Few if any MSSPs have any real skin in the game when it comes to compliance. Read their statement of work and it is lightly mentioned if at all and there are caveats galore around why they are not responsible or accountable in any meaningful way. In many cases, MSSPs introduce their own set of issues, vulnerabilities, and compliance headaches because the MSSP is not properly equipped to manage data and processes in a manner aligned with CMMC requirements. With the MSSP handling most every piece of security and monitoring but never documenting and attesting compliance with CMMC, the current MSSP model falls short of CMMC requirements.
Investing in CMMC compliance (which includes compliance with DFARS 7012 and NIST 800-171) is a big effort because it now includes line of business systems including finance, personnel, and IT vulnerability information. While MSSPs are valuable partners who reduce overhead costs and enable businesses to stay focused on their core mission, it is important to remember that MSSPs will have access to documents, CUI, and data including passwords, access codes, and vulnerability information about their IT environment. Because MSSPs have this kind of sensitive data in their possession, it is critical that they make the same investment in NIST 800-171 to ensure that you stay compliant and properly manage CUI information and the security of your IT environment. Again, most MSSPs have very little if anything in their statements of work regarding compliance so small businesses are left with a false sense of security around achieving CMMC compliance.
Without clear lines of responsibilities between the owner of compliance and the business and IT operations of the host company, the failure of a compliance audit is inevitable.
That is the bad news, now for the good news.
CyberSheath’s Managed CMMC Service
In response to the new federal requirements and an ever-changing landscape, CyberSheath has created a whole new set of Managed Services to allow for any business to achieve any CMMC compliance level they desire. Unlike every other MSSP in the market today our CMMC service offerings are an evolution of our successful legacy NIST 800-171 Managed Services. Said another way, we aren’t new to this space and we have been through dozens of successful third-party audits over the past five-plus years.
We offer 5 different levels of assured compliance for you to choose from based on your business requirements. To date, 100% of our customers are focused on CMMC Maturity Level (ML) 3 as it so closely aligns with the NIST 800-171 requirements.
First Step:
- We meet your business where it is today. We will gain visibility of your desired CMMC ML and any gaps in processes, documentation, practices, or technology.
- Gain current and ongoing visibility into NIST 800-171 / CMMC via professional certified assessments and remediation plans.
Second Step – Select Hosted Compliance Level(s):
- Level 1: Become compliant with CMMC ML1 over your entire infrastructure within weeks.
- Level 2: Work with a virtual security officer and get assistance with ongoing compliance program oversight and routine reporting.
- Level 3: Quickly gain the ability to achieve compliance and bid on CMMC ML3 contracts with our cloud-based guaranteed compliance offering.
- Level 4 or Level 5: Leverage our expertise as we maintain the rigorous program, technology, engineering, and implementation required for the most robust security standards.
- Beyond:
- Future-proof your compliance to changes in CMMC policy or implementation approaches by assigning ongoing program maintenance to CyberSheath.
- High Cloud infrastructure in a hosted compliant process.
Third Step: We manage your compliance as an outsourced compliance program inclusive of an MSSP
CyberSheath’s CMMC Shared Security Model is the Answer to CMMC Compliance for Small Businesses
Whether it be a public, private, or hybrid architecture, businesses must take responsibility for ensuring that their data is secure. With limited resources and no time to become a CMMC expert, the solution to the problem is clearly a shared responsibility model. CyberSheath has successfully implemented and been audited against our shared responsibility model many times over the last five-plus years so our solution is tested and audit-ready. Our tailored responsibility matrix eliminates single points of failure and ensures that all required security requirements have an owner and produce the required documentation and evidence. The shared responsibility model reduces the day-to-day operational demands on your business and ensures documented, repeatable, and audit-ready compliance.
With government revenues on the line, it is crucial to determine who controls the various components of the CMMC compliant infrastructure and operations. CyberSheath defines where and how security measures should be applied, with a special focus on CUI and other sensitive government data.
CyberSheath differentiates itself by taking ownership of assured CMMC compliance and it is a contractual requirement that we put right into our statements of work. This cannot be done in isolation and requires shared and distinct responsibilities on both sides of the partnership which tend to be specific to each company. CyberSheath offers a ‘single-pane-of-glass’ to gain visibility into CMMC compliance, continuous security monitoring, and various important datasets, analytics, and user interfaces in one place. Our CMMC management platform is built around Microsoft Azure’s FedRAMP GCC High environment which ensures infrastructure capabilities that can detect and remedy security misconfigurations, leveraging services to ensure near-real-time compliance features.
Why CyberSheath?
Cybersheath has leveraged and lived this Shared Responsibility Model for NIST 800-171 successfully for many years now, and expect that it will be a fundamental part of CMMC attestation and MSSP partnerships going forward. The experts at CyberSheath understand your challenges – and we can help. Contact us to make sure your CMMC readiness gets – and stays – on track.